I’ll be bold and state that ‘Ransomware is the most significant IT security risk to SMB’s’….
It would be exactly the same for Enterprise sized organisations, but these typically have better contingency and Disaster Recovery procedures to clear the mess if they are hit.
To start at the beginning – for those not familiar, Ransomware is a type of Malware, Malware is short for ‘Malicious Software’ and Malicious Software is the general term used to describe things like Viruses, Trojans, Worms and all the other software that the many people usually just call ‘Viruses’.
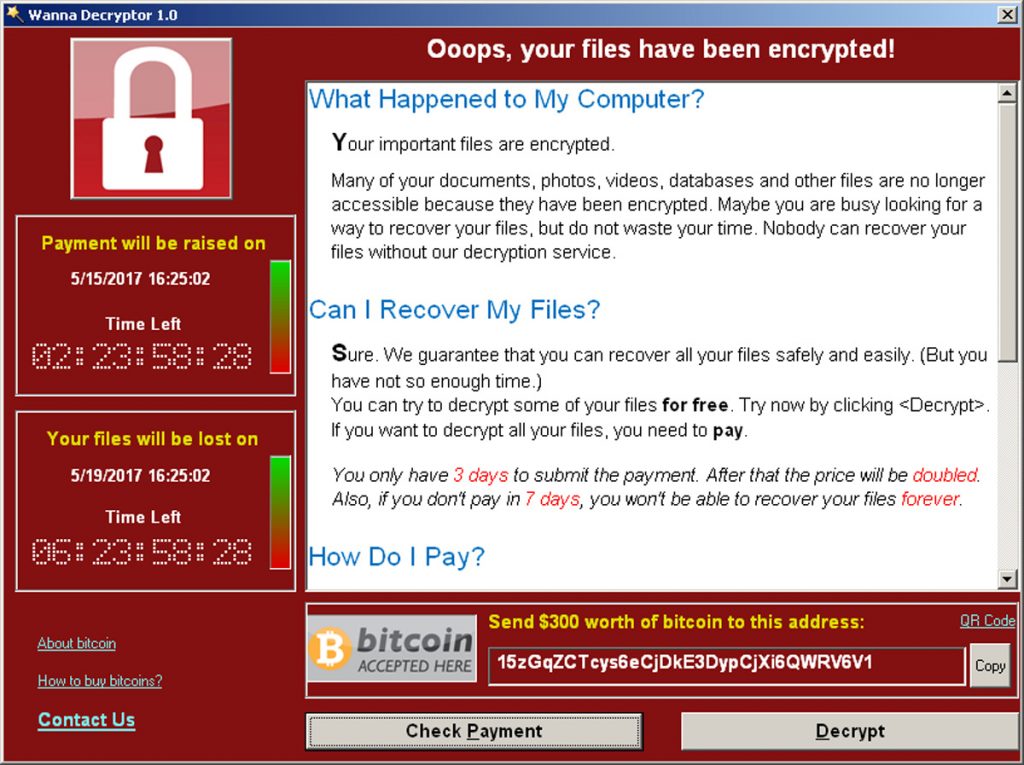
To provide a common example, Ransomware generally works like this…. A recipient receives an email that looks like it is legitimate and has some enticing words to get you to click a link. Nothing new here, social engineering has been used to distribute malware for a long time. What has changed is that the email used to have an attachment often called something like ‘Pamela Anderson’ to entice the reader to click; however, attackers have become smarter, the email is much more likely to look like it has come from something like Paypal, and referring to a transaction you don’t recognise. ‘Click here to cancel’ has all the more draw, if you think there is a risk to your finances if you ignore it! When you click the link, it directs you to a website that uses one of many techniques to install or run a program on your device that starts to encrypt your files (sometimes with a delay to avoid detection). It will usually also drop a file somewhere, that is not encrypted, and provides you with your very own guide to what has just happened, and how to retrieve your files. Attacks can also happen via USB stick, visiting a website “drive by attack”, social media, Internet of Things, mobile devices or even fileless attacks – more on these later.
In all probability, the instructions relating to where to send your money, will be pretty accurate. However, the guide as to whether and how you will get access to your files, has proven to be less so!
To watch a Ransomware attack in real time, see our 4-minute YouTube video here
So why do I believe this is one of the most significant data security risks? – because with Ransomware there is no going back. Once infected, to use an idiom ‘You’re damned if you do, damned if you don’t’. Pay up – and research shows you have about a 30% chance of getting your data back, don’t pay up, and you have lost your data!
At this point you are reliant on the honour of your cybercriminal, or your ability to get the data from your backups…
Big business will (hopefully) have a reliable well thought out backup / restore process, so though they now have to go through the cycle of restoration. Whilst inconvenient, and likely to cause short term challenges, it is still an occurrence that is likely to have been planned for.
For many small businesses the challenge is greater.
Backup solutions remain expensive so most small businesses usually take the most cost effective route and utilise solutions such as cloud, USB, or hardware (NAS/SAN) storage due to such solutions having generally fallen in price over recent years. However, these technologies are as equally susceptible to ransomware as your hard drive is – i.e.when the storage you are using for your primary backup is always available (either via a cloud sync program (o365, Dropbox Sync agent etc) or via a shared drive such as presented by a USB HDD, NAS or SAN, it will also be infected by the Ransomware, just like your local HDD, the moment the attack occurs. In fact, most Ransomware look for network drives before they encrypt your local drive as they know this is also where you are likely to keep your most important information, and organisations are less likely to pay a ransom for a single encrypted laptop.
So, there is a risk that the very backup you need to use to get out of trouble has itself been encrypted. Now many people who work day in day out with backups will be screaming at this article, about how important it is to keep your backups off line (un-plugged, at a different location), and they are right. But for many small businesses, who have very limited IT resource, we know this does not always happen!
For those of you that recognise the scenario I am talking about, you may be thinking “Dropbox (or another) have told me they backup my Data, so I am sure I am OK” – well my response is, that they ‘may’ backup your data. But then again, they may not. Cloud services often provide a number of snapshots, and backup incremental changes to data. However, they also have their own retention policies. So where older files have not been updated for a while, there is a very real chance that Dropbox (or another) may not have the backups of your data that you think they do. If you are using multiple cloud services like this, they may all be running different variations to their recovery procedures, and you may never know if you are fully covered until your data has gone!
This complexity is why Backup Vendors still exist, and why a large company would never rely on the ‘built in’ functionality without thoroughly testing all eventualities… regularly!
So what can you do….
In addition to all of the best practice (such as teaching your staff not to click links, storing data in the right places) and the existing tools you have for Malware and Anti-Virus in general, larger companies are now taking specific action to protect against Ransomware – such technologies are now becoming readily available to the SMB market.
Stop Ransomware arriving –
This is often achieved using detection methods at the Endpoint (PC). Either looking for Malware in General, or specifically looking for Ransomware. This is usually straightforward, as your current Anti-Virus solution will offer some protection, and they will also likely have some additional tools specifically targeted at Ransomware. We like (& sell) Sophos, and they have 2 solutions which help provide some Ransomware protection: their standard Anti Virus product provides built-in Malware (and therefore Ransomware) protection. Then there is a product called Intercept X specifically designed to provide excellent detection and protection techniques of Ransomware.
However, there may still be some gaps and vulnerable areas – there are more and more devices on your Network that do not have your corporate Anti-Virus installed (Guest Users, Mobile devices / Phones, and of course IOT – (Wifi, Printers, Photocopiers, Alarm Systems etc etc) If any of these are infected, they could go undetected. Even on standard pc’s there is a very real risk that your perimeter and endpoint protection will miss some malware. And if for instance a ransomware passes your first line of defence, that same ransomware is now free to start encrypting your environment and fileshares.
If Endpoint Security was effective all of the time, we would not see Ransomware as prevalent as it is. So what else can we do to protect our central environment and fileshares:
Stop Ransomware Encrypting
If Ransomware gets through your first lines of defence (The Endpoint Security/AV) and starts to encrypt data on your network, it does not take long to cause havoc. Ransomware is become more and more sophisticated, and is becoming able to bypass server anti-virus agents.
However, there is a last line of defence option – a solution which works in parallel with your AV.
We are working Bullwall, who’s Ransomcare solution is specifically targeted at stopping Ransomware that has made it past your first line of defence (the Anti-Virus).
Bullwall’s ‘Ransomcare’ product has been specifically designed to continually watch for the behaviours shown by Ransomware, by monitoring your fileshares and files for illegitimate encryption, and then shutdown the source of an attack, before the attack takes hold, providing organisations with the protection they hope for.
Restore Encrypted Data
And let’s not forget. An offline backup/restore, which is tested regularly, remains one of the most important elements in the provision of recovering your data for all sizes of business. This is often your last line of hope. However, the criminals are getting wise to this, and developing Ransomware that lays dormant until it is well embedded in your backups, even making recovery from tape no longer the ultimate protection that it once was.
Call us on 03300 53 59 55 to talk about protecting your IT from Ransomware.

































